I’m into computer security a little bit and always striving to learn more. I’m also a firm believer in Open Source software. In Proprietary software you don’t know really know what’s going on. Case in point: Alexa, Siri, Hey Google. They say it isn’t spying on you but you know that it is.
With Open Source software you can view the code and see if any hanky panky is going on.
There are a lot of Open Source Operating Systems such a Linux. But here’s the catch. You run your Open Source OS which gets launched by a firmware (BIOS – Built In Operating System) which is PROPRIETARY!. Also it can prevent you from installing a 3rd party device such as a battery, or charging brick. Major exploits such as HeartBleed (remember that scare a few years ago) live and breathe in the firmware. You can slick the OS, change the hard drive all you want but you are still compromised AND YOU DON’T EVEN KNOW IT.
Let’s lay out a scenario.
I had a hardware firewall from a company called Netgate and it runs software called pfSense which is basically FreeBSD Unix. Netgate sells the hardware with the software installed. Netgate also allows you to run an Open Source BIOS called Coreboot.
What’s the downside here? Not much except for COST. Netgate sells you overpriced hardware. No doubt about it. You can get firewall appliances for a fraction of the cost and install pfSense yourself.
So I did that. I bought an appliance DIRECTLY FROM CHINA.
It was dirt cheap and it had pfSense on it as well. So I formatted the drive and did a fresh install of pfSense myself and felt like I accomplished something. The reality is my firewall appliance COULD be compromised with a Chinese BIOS. I don’t know, I’m not sure, but it could be. Since I learned about Coreboot I am just not taking any chances anymore.
I bought a new appliance from a company called ProtectLI. You can get the firewall pre-configured with the latest version of Coreboot and best of all they release pre-built firmware upgrades as new Coreboot versions are pushed out.

ProtectLI Vault 4 FW4B
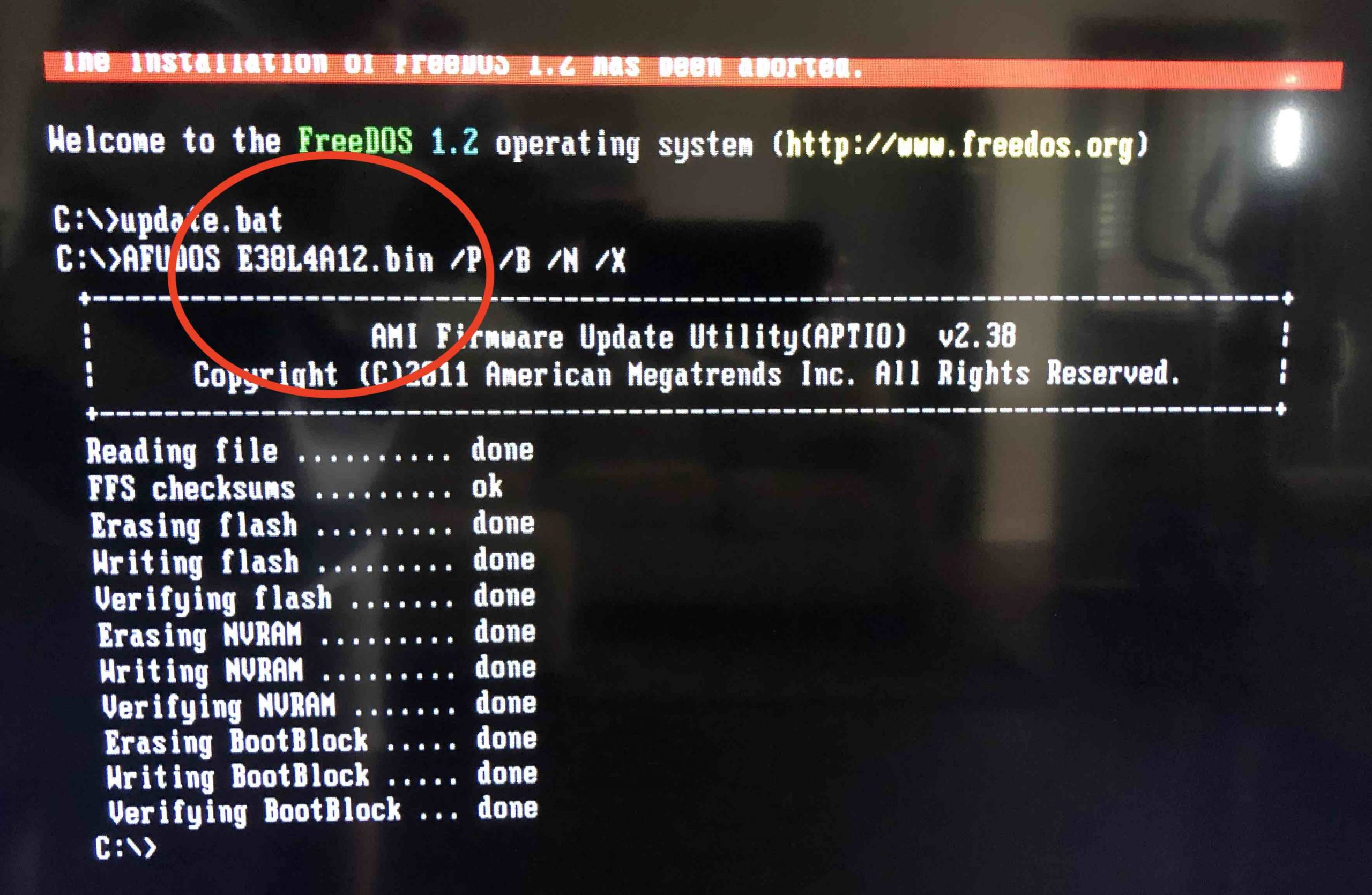
Speaking of ProtectLI……..they seem to sell the exact same appliance as my original purchase from China. Exactly Exact as a matter of fact. I went to their website and downloaded the BIOS for a FW4A appliance and ensured the BIOS ID was the same (with the exception of the version number). It was so I made a FreeDOS bootable drive and flashed the firmware to the latest version. It worked. So I feel a little better about the security of the device. The BIOS version I had was A02 and I updated it to A12 which was quite a leap. Having rewritten the firmware with a more recent BIOS from a reputable company……….I feel better now.
Since I won’t put Coreboot on this older appliance I did go ahead and install Ubuntu 20.04 LTS on it. Works great and I’ll find a job for this device soon rather than toss it in the closet.
The other strategy would be to pay the big money to buy a Netgate Appliance and in fact, Netgate also allows you to maintain the latest Coreboot upgrades.
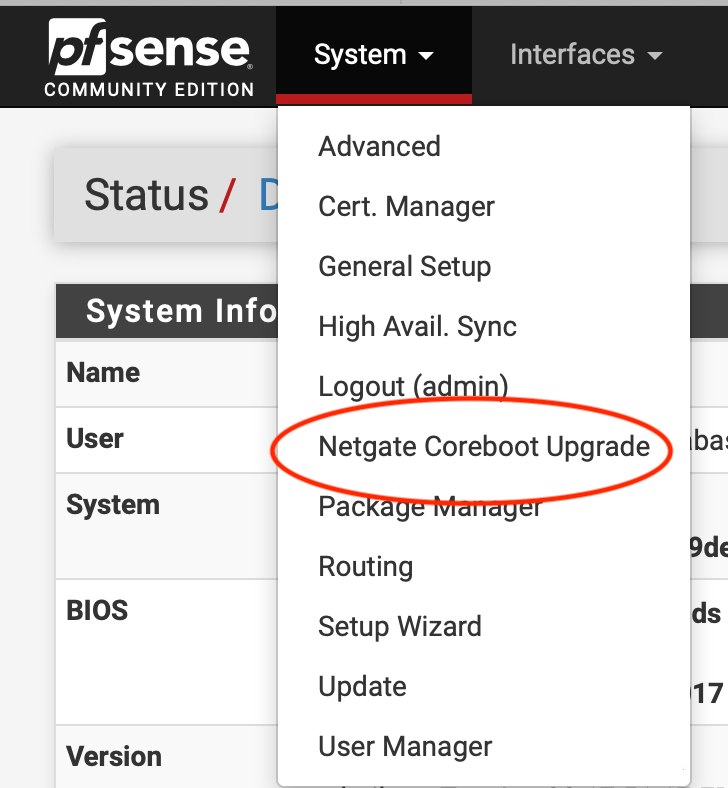
Netgate Coreboot Upgrade
It is my considered tech-geek opinion that no one should be running a hardware firewall appliance that does NOT run Coreboot.
The Coreboot hardware compatibility list is far from all inclusive though. You need to make sure your hardware will accept it and unless you can get it pre-configured like with ProtectLI it is somewhat difficult to install and must be built from source.
Not impossible, and there are good tutorials out there, but it is a step or two above the abilities of most casual computer geeks.
Still, it is a worthwhile endeavor that will give you peace of mind and inherently better security. It allows you to change hardware configurations and it is MUCH FASTER than legacy BIOS’s like AMI.
In the interim until the new firewall appliance with Coreboot shows up I dug my Netgate SG-2220 appliance out of the closet, put a fresh installation of pfSense on it and restored a backup file. To my surprise the SG-2220 was already running Coreboot all these years. I should have left well enough alone.
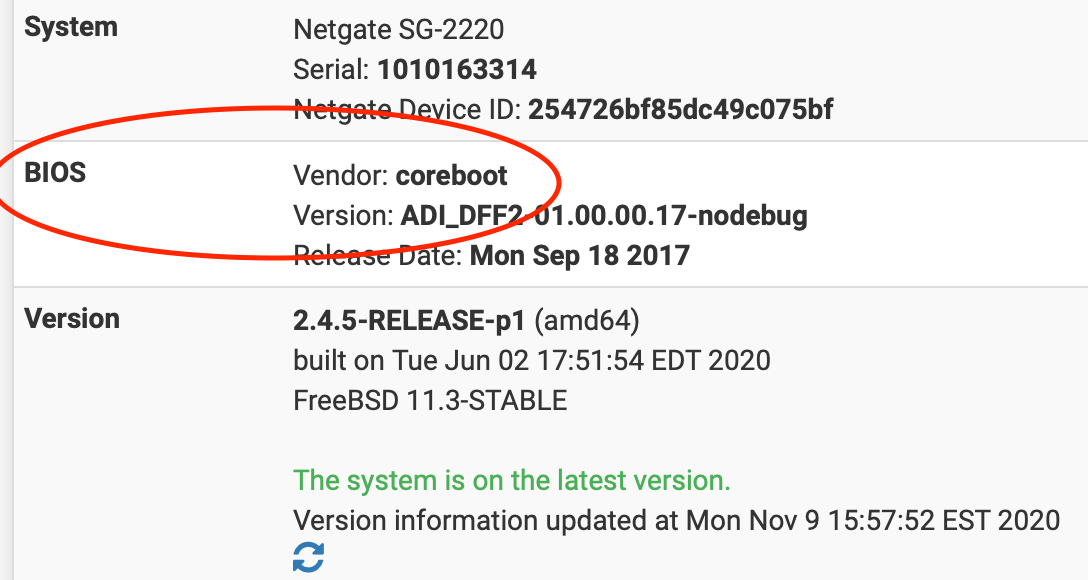
Coreboot on Netgate SG-2220
Anyway, if you learned anything today it should be that an Open Source OS really needs to sit on top of an Open Source firmware for maximum security.

Thanks for getting back to a tech post! We have similar interests (network security, ham radio, SDR, scanner monitoring, home automation, modding things to do different stuff, etc) but not bikes. (even though I should!!) 🙂 BTW, I don’t remember if you have covered it but have you checked out Trunk Recorder and OpenMHZ? If not, you should. Good stuff! Thanks again and 73s.
N9OHA