My OpenVPN Connect app on my iPhone just quit working. This is how I kicked its ass.
I have been a big fan of Virtual Private Networks for YEARS. If you are on an untrusted connection such as Airport or Hotel or Coffee Shop the safe play is to connect to a VPN which encrypts your communications in a tunnel between your computer and your VPN server. It wildly increases security.
So for years I have run an OpenVPN server on my hardwire firewall which runs an OS called pfSense. If you have any inkling of security at all you should run a hardware firewall. But that is a discussion for another day. Anyway pfSense has an easy configuration for OpenVPN with a client export feature that is second to none.
However, the IOS OpenVPN app JUST QUIT WORKING. I can connect to my VPN but traffic doesn’t seem to move. I can’t do anything with it at all. So I hit the OpenVPN IOS forum and sure enough……..this is a thing. Since October 2018 as well! To confirm this is the problem I can connect to my OpenVPN server JUST FINE with my iPads which have the older app.
I am at the mercy of OpenVPN to fix this. However, I have pretty extensive home automation and I just poured my heart and soul into controlling such things as the garage door from afar and now I can’t.

Okay. John is fed up. I tried everything to make OpenVPN Connect app work and it just won’t.
I will just set up another VPN!
In pfSense there is the option of creating an IPsec VPN which is also very secure, and very fast.
Let’s do this. In pfSense navigate to VPN > IPsec > Mobile Clients
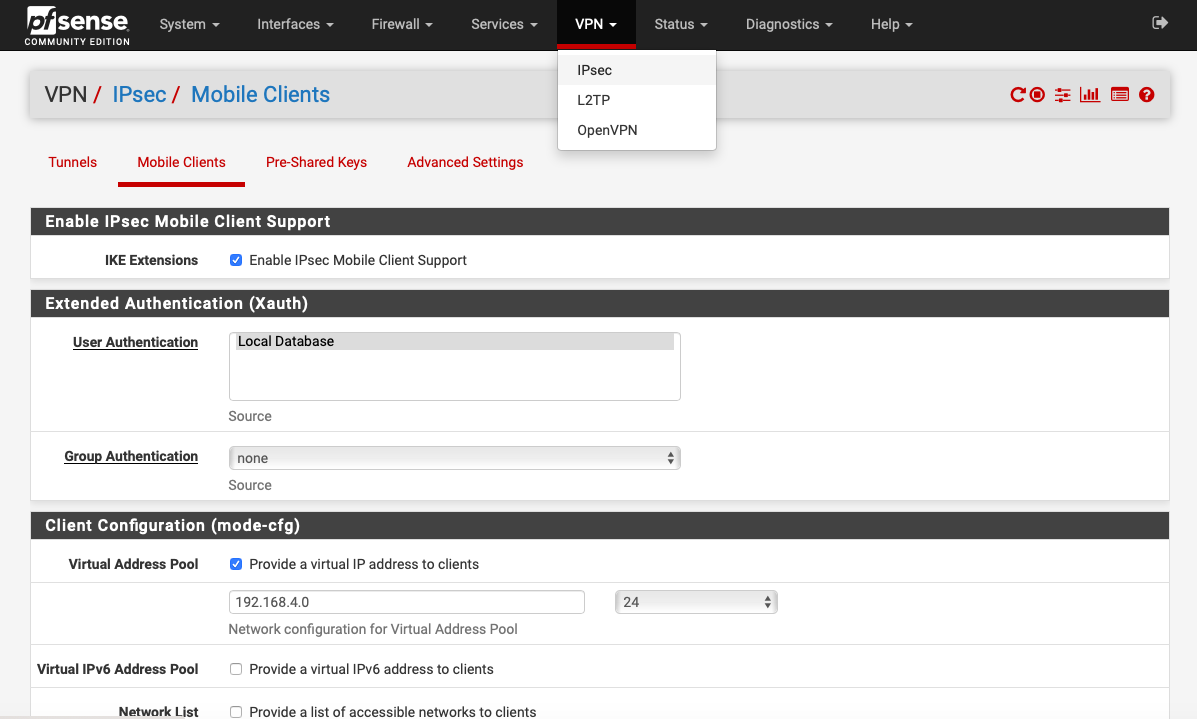
Now fill out the Mobile Clients page like below and realize that if I didn’t mention it to leave it as the default setting.
MOBILE CLIENTS
IKE Extensions Enable IPsec Mobile Client Support = checked User Authentication = Local Database Group Authentication = none Virtual Address Pool = checked 192.168.4.0/24 All others unchecked Login Banner (optional) = Success
Now it should tell you to apply and to create a Phase 1. Here are the Phase 1 settings under VPN > IPsec
PHASE 1
PHASE 1 Key Exchange version = IKEv1 Internet Protocol = IPv4 Interface = WAN Authentication Method = Mutual PSK + Xauth Negotiation Mode = Aggressive My identifier = My IP address Peer Identifier = User distinguished name (I just used my email here) Pre-Shared Key = You make it up. Make a long random string of characters. Encryption Algorithm = AES, 128 bits, SHA1, 2(1024 bit) Lifetime = (3600) NAT Traversal = Auto Dead Peer Detection = checked Delay 10 Max Failures = 5
Now at the end of Phase 1 create a Phase 2
PHASE 2
Mode = Tunnel IPv4 Local Network = Network Address = 0.0.0.0/0 NAT/BINAT translation = None Description IOS Protocol = ESP Encryption Algorithms = AES checked, set to Auto Hash Algorithms = SHA1 checked PFS key group = off Lifetime 86400
On to the User Manager (System > User Manager)
USER MANAGER
Create a User that has the following effective Privileges. I used my existing account which already had the WebCfg stuff and just added the VPN IPsec xauth Dialin
| admins | WebCfg – All pages | Allow access to all pages (admin privilege) | |
| User – VPN: IPsec xauth Dialin | Indicates whether the user is allowed to dial in via IPsec xauth (Note: Does not allow shell access, but may allow the user to create SSH tunnels) |
Now for the iPhone. Navigate to VPN under general and add a VPN with the following settings:
Type = IPsec Server = IP address of server or FQDN Account = User name Password = the account user above’s password Group Name = Peer Identifier in Phase 1 () Secret = Pre Shared Key (PSK) in Phase 1 above (long string of random characters).
Try to connect!
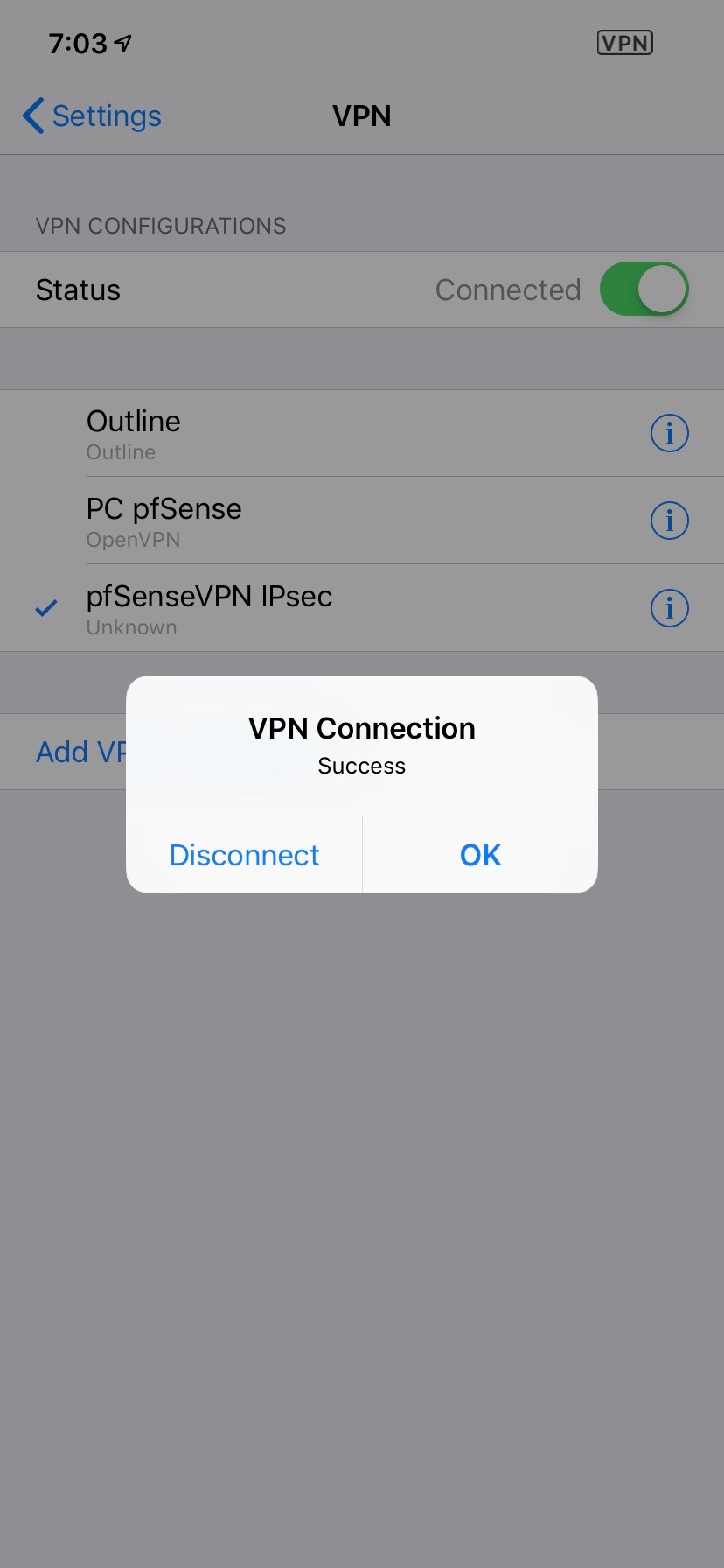
And there we have it! VPN ON!

F Yeah!
Unfortunately it did not work for me, error message:”VPN Connection – The VPN server did not respond.”
I followed, and it worked. However I did have to make two changes, which you may want to note for others.
1) The network should be something different than your local (up one subnet)
2) You need a firewall rule to allow traffic from ipsec to you lan
Thanks for the write up
Thank you for the write up! Everything worked for me with the exception that I had to enable “Provide a DNS server list to clients” in the mobile client options, and then had to set two DNS servers. Anyone else experience that?